搜索到
37
篇与
linux
的结果
-
 iptables管理脚本 #!/bin/sh # # iptablesStart iptables firewall # # chkconfig: 2345 08 92 # description:Starts, stops and saves iptables firewall # # config: /etc/sysconfig/iptables # config: /etc/sysconfig/iptables-config # ### BEGIN INIT INFO # Provides: iptables # Required-Start: # Required-Stop: # Default-Start: 2 3 4 5 # Default-Stop: 0 1 6 # Short-Description: start and stop iptables firewall # Description: Start, stop and save iptables firewall ### END INIT INFO # Source function library. . /etc/init.d/functions IPTABLES=iptables IPTABLES_DATA=/etc/sysconfig/$IPTABLES IPTABLES_FALLBACK_DATA=${IPTABLES_DATA}.fallback IPTABLES_CONFIG=/etc/sysconfig/${IPTABLES}-config IPV=${IPTABLES%tables} # ip for ipv4 | ip6 for ipv6 [ "$IPV" = "ip" ] && _IPV="ipv4" || _IPV="ipv6" PROC_IPTABLES_NAMES=/proc/net/${IPV}_tables_names VAR_SUBSYS_IPTABLES=/var/lock/subsys/$IPTABLES # only usable for root if [ $EUID != 0 ]; then echo -n $"${IPTABLES}: Only usable by root."; warning; echo exit 4 fi if [ ! -x /sbin/$IPTABLES ]; then echo -n $"${IPTABLES}: /sbin/$IPTABLES does not exist."; warning; echo exit 5 fi # Old or new modutils /sbin/modprobe --version 2>&1 | grep -q module-init-tools \ && NEW_MODUTILS=1 \ || NEW_MODUTILS=0 # Default firewall configuration: IPTABLES_MODULES="" IPTABLES_MODULES_UNLOAD="yes" IPTABLES_SAVE_ON_STOP="no" IPTABLES_SAVE_ON_RESTART="no" IPTABLES_SAVE_COUNTER="no" IPTABLES_STATUS_NUMERIC="yes" IPTABLES_STATUS_VERBOSE="no" IPTABLES_STATUS_LINENUMBERS="yes" IPTABLES_SYSCTL_LOAD_LIST="" # Load firewall configuration. [ -f "$IPTABLES_CONFIG" ] && . "$IPTABLES_CONFIG" # Netfilter modules NF_MODULES=($(lsmod | awk "/^${IPV}table_/ {print \$1}") ${IPV}_tables) NF_MODULES_COMMON=(x_tables nf_nat nf_conntrack) # Used by netfilter v4 and v6 # Get active tables NF_TABLES=$(cat "$PROC_IPTABLES_NAMES" 2>/dev/null) rmmod_r() { # Unload module with all referring modules. # At first all referring modules will be unloaded, then the module itself. local mod=$1 local ret=0 local ref= # Get referring modules. # New modutils have another output format. [ $NEW_MODUTILS = 1 ] \ && ref=$(lsmod | awk "/^${mod}/ { print \$4; }" | tr ',' ' ') \ || ref=$(lsmod | grep ^${mod} | cut -d "[" -s -f 2 | cut -d "]" -s -f 1) # recursive call for all referring modules for i in $ref; do rmmod_r $i let ret+=$?; done # Unload module. # The extra test is for 2.6: The module might have autocleaned, # after all referring modules are unloaded. if grep -q "^${mod}" /proc/modules ; then modprobe -r $mod > /dev/null 2>&1 res=$? [ $res -eq 0 ] || echo -n " $mod" let ret+=$res; fi return $ret } flush_n_delete() { # Flush firewall rules and delete chains. [ ! -e "$PROC_IPTABLES_NAMES" ] && return 0 # Check if firewall is configured (has tables) [ -z "$NF_TABLES" ] && return 1 echo -n $"${IPTABLES}: Flushing firewall rules: " ret=0 # For all tables for i in $NF_TABLES; do # Flush firewall rules. $IPTABLES -t $i -F; let ret+=$?; # Delete firewall chains. $IPTABLES -t $i -X; let ret+=$?; # Set counter to zero. $IPTABLES -t $i -Z; let ret+=$?; done [ $ret -eq 0 ] && success || failure echo return $ret } set_policy() { # Set policy for configured tables. policy=$1 # Check if iptable module is loaded [ ! -e "$PROC_IPTABLES_NAMES" ] && return 0 # Check if firewall is configured (has tables) tables=$(cat "$PROC_IPTABLES_NAMES" 2>/dev/null) [ -z "$tables" ] && return 1 echo -n $"${IPTABLES}: Setting chains to policy $policy: " ret=0 for i in $tables; do echo -n "$i " case "$i" in raw) $IPTABLES -t raw -P PREROUTING $policy \ && $IPTABLES -t raw -P OUTPUT $policy \ || let ret+=1 ;; filter) $IPTABLES -t filter -P INPUT $policy \ && $IPTABLES -t filter -P OUTPUT $policy \ && $IPTABLES -t filter -P FORWARD $policy \ || let ret+=1 ;; nat) $IPTABLES -t nat -P PREROUTING $policy \ && $IPTABLES -t nat -P POSTROUTING $policy \ && $IPTABLES -t nat -P OUTPUT $policy \ || let ret+=1 ;; mangle) $IPTABLES -t mangle -P PREROUTING $policy \ && $IPTABLES -t mangle -P POSTROUTING $policy \ && $IPTABLES -t mangle -P INPUT $policy \ && $IPTABLES -t mangle -P OUTPUT $policy \ && $IPTABLES -t mangle -P FORWARD $policy \ || let ret+=1 ;; *) let ret+=1 ;; esac done [ $ret -eq 0 ] && success || failure echo return $ret } load_sysctl() { # load matched sysctl values if [ -n "$IPTABLES_SYSCTL_LOAD_LIST" ]; then echo -n $"Loading sysctl settings: " ret=0 for item in $IPTABLES_SYSCTL_LOAD_LIST; do fgrep $item /etc/sysctl.conf | sysctl -p - >/dev/null let ret+=$?; done [ $ret -eq 0 ] && success || failure echo fi return $ret } start() { # Do not start if there is no config file. if [ ! -f "$IPTABLES_DATA" ]; then echo -n $"${IPTABLES}: No config file."; warning; echo return 6 fi # check if ipv6 module load is deactivated if [ "${_IPV}" = "ipv6" ] \ && grep -qIsE "^install[[:space:]]+${_IPV}[[:space:]]+/bin/(true|false)" /etc/modprobe.conf /etc/modprobe.d/* ; then echo $"${IPTABLES}: ${_IPV} is disabled." return 150 fi echo -n $"${IPTABLES}: Applying firewall rules: " OPT= [ "x$IPTABLES_SAVE_COUNTER" = "xyes" ] && OPT="-c" $IPTABLES-restore $OPT $IPTABLES_DATA if [ $? -eq 0 ]; then success; echo else failure; echo; if [ -f "$IPTABLES_FALLBACK_DATA" ]; then echo -n $"${IPTABLES}: Applying firewall fallback rules: " $IPTABLES-restore $OPT $IPTABLES_FALLBACK_DATA if [ $? -eq 0 ]; then success; echo else failure; echo; return 1 fi else return 1 fi fi # Load additional modules (helpers) if [ -n "$IPTABLES_MODULES" ]; then echo -n $"${IPTABLES}: Loading additional modules: " ret=0 for mod in $IPTABLES_MODULES; do echo -n "$mod " modprobe $mod > /dev/null 2>&1 let ret+=$?; done [ $ret -eq 0 ] && success || failure echo fi # Load sysctl settings load_sysctl touch $VAR_SUBSYS_IPTABLES return $ret } stop() { # Do not stop if iptables module is not loaded. [ ! -e "$PROC_IPTABLES_NAMES" ] && return 0 # Set default chain policy to ACCEPT, in order to not break shutdown # on systems where the default policy is DROP and root device is # network-based (i.e.: iSCSI, NFS) set_policy ACCEPT # And then, flush the rules and delete chains flush_n_delete if [ "x$IPTABLES_MODULES_UNLOAD" = "xyes" ]; then echo -n $"${IPTABLES}: Unloading modules: " ret=0 for mod in ${NF_MODULES[*]}; do rmmod_r $mod let ret+=$?; done # try to unload remaining netfilter modules used by ipv4 and ipv6 # netfilter for mod in ${NF_MODULES_COMMON[*]}; do rmmod_r $mod >/dev/null done [ $ret -eq 0 ] && success || failure echo fi rm -f $VAR_SUBSYS_IPTABLES return $ret } save() { # Check if iptable module is loaded if [ ! -e "$PROC_IPTABLES_NAMES" ]; then echo -n $"${IPTABLES}: Nothing to save."; warning; echo return 0 fi # Check if firewall is configured (has tables) if [ -z "$NF_TABLES" ]; then echo -n $"${IPTABLES}: Nothing to save."; warning; echo return 6 fi echo -n $"${IPTABLES}: Saving firewall rules to $IPTABLES_DATA: " OPT= [ "x$IPTABLES_SAVE_COUNTER" = "xyes" ] && OPT="-c" ret=0 TMP_FILE=$(/bin/mktemp -q $IPTABLES_DATA.XXXXXX) \ && chmod 600 "$TMP_FILE" \ && $IPTABLES-save $OPT > $TMP_FILE 2>/dev/null \ && size=$(stat -c '%s' $TMP_FILE) && [ $size -gt 0 ] \ || ret=1 if [ $ret -eq 0 ]; then if [ -e $IPTABLES_DATA ]; then cp -f $IPTABLES_DATA $IPTABLES_DATA.save \ && chmod 600 $IPTABLES_DATA.save \ && restorecon $IPTABLES_DATA.save \ || ret=1 fi if [ $ret -eq 0 ]; then mv -f $TMP_FILE $IPTABLES_DATA \ && chmod 600 $IPTABLES_DATA \ && restorecon $IPTABLES_DATA \ || ret=1 fi fi rm -f $TMP_FILE [ $ret -eq 0 ] && success || failure echo return $ret } status() { if [ ! -f "$VAR_SUBSYS_IPTABLES" -a -z "$NF_TABLES" ]; then echo $"${IPTABLES}: Firewall is not running." return 3 fi # Do not print status if lockfile is missing and iptables modules are not # loaded. # Check if iptable modules are loaded if [ ! -e "$PROC_IPTABLES_NAMES" ]; then echo $"${IPTABLES}: Firewall modules are not loaded." return 3 fi # Check if firewall is configured (has tables) if [ -z "$NF_TABLES" ]; then echo $"${IPTABLES}: Firewall is not configured. " return 3 fi NUM= [ "x$IPTABLES_STATUS_NUMERIC" = "xyes" ] && NUM="-n" VERBOSE= [ "x$IPTABLES_STATUS_VERBOSE" = "xyes" ] && VERBOSE="--verbose" COUNT= [ "x$IPTABLES_STATUS_LINENUMBERS" = "xyes" ] && COUNT="--line-numbers" for table in $NF_TABLES; do echo $"Table: $table" $IPTABLES -t $table --list $NUM $VERBOSE $COUNT && echo done return 0 } reload() { # Do not reload if there is no config file. if [ ! -f "$IPTABLES_DATA" ]; then echo -n $"${IPTABLES}: No config file."; warning; echo return 6 fi # check if ipv6 module load is deactivated if [ "${_IPV}" = "ipv6" ] \ && grep -qIsE "^install[[:space:]]+${_IPV}[[:space:]]+/bin/(true|false)" /etc/modprobe.conf /etc/modprobe.d/* ; then echo $"${IPTABLES}: ${_IPV} is disabled." return 150 fi echo -n $"${IPTABLES}: Trying to reload firewall rules: " OPT= [ "x$IPTABLES_SAVE_COUNTER" = "xyes" ] && OPT="-c" $IPTABLES-restore $OPT $IPTABLES_DATA if [ $? -eq 0 ]; then success; echo else failure; echo; echo "Firewall rules are not changed."; return 1 fi # Load additional modules (helpers) if [ -n "$IPTABLES_MODULES" ]; then echo -n $"${IPTABLES}: Loading additional modules: " ret=0 for mod in $IPTABLES_MODULES; do echo -n "$mod " modprobe $mod > /dev/null 2>&1 let ret+=$?; done [ $ret -eq 0 ] && success || failure echo fi # Load sysctl settings load_sysctl return $ret } restart() { [ "x$IPTABLES_SAVE_ON_RESTART" = "xyes" ] && save stop start } case "$1" in start) [ -f "$VAR_SUBSYS_IPTABLES" ] && exit 0 start RETVAL=$? ;; stop) [ "x$IPTABLES_SAVE_ON_STOP" = "xyes" ] && save stop RETVAL=$? ;; restart|force-reload) restart RETVAL=$? ;; reload) [ -e "$VAR_SUBSYS_IPTABLES" ] && reload RETVAL=$? ;; condrestart|try-restart) [ ! -e "$VAR_SUBSYS_IPTABLES" ] && exit 0 restart RETVAL=$? ;; status) status RETVAL=$? ;; panic) set_policy DROP RETVAL=$? ;; save) save RETVAL=$? ;; *) echo $"Usage: ${IPTABLES} {start|stop|reload|restart|condrestart|status|panic|save}" RETVAL=2 ;; esac exit $RETVAL
iptables管理脚本 #!/bin/sh # # iptablesStart iptables firewall # # chkconfig: 2345 08 92 # description:Starts, stops and saves iptables firewall # # config: /etc/sysconfig/iptables # config: /etc/sysconfig/iptables-config # ### BEGIN INIT INFO # Provides: iptables # Required-Start: # Required-Stop: # Default-Start: 2 3 4 5 # Default-Stop: 0 1 6 # Short-Description: start and stop iptables firewall # Description: Start, stop and save iptables firewall ### END INIT INFO # Source function library. . /etc/init.d/functions IPTABLES=iptables IPTABLES_DATA=/etc/sysconfig/$IPTABLES IPTABLES_FALLBACK_DATA=${IPTABLES_DATA}.fallback IPTABLES_CONFIG=/etc/sysconfig/${IPTABLES}-config IPV=${IPTABLES%tables} # ip for ipv4 | ip6 for ipv6 [ "$IPV" = "ip" ] && _IPV="ipv4" || _IPV="ipv6" PROC_IPTABLES_NAMES=/proc/net/${IPV}_tables_names VAR_SUBSYS_IPTABLES=/var/lock/subsys/$IPTABLES # only usable for root if [ $EUID != 0 ]; then echo -n $"${IPTABLES}: Only usable by root."; warning; echo exit 4 fi if [ ! -x /sbin/$IPTABLES ]; then echo -n $"${IPTABLES}: /sbin/$IPTABLES does not exist."; warning; echo exit 5 fi # Old or new modutils /sbin/modprobe --version 2>&1 | grep -q module-init-tools \ && NEW_MODUTILS=1 \ || NEW_MODUTILS=0 # Default firewall configuration: IPTABLES_MODULES="" IPTABLES_MODULES_UNLOAD="yes" IPTABLES_SAVE_ON_STOP="no" IPTABLES_SAVE_ON_RESTART="no" IPTABLES_SAVE_COUNTER="no" IPTABLES_STATUS_NUMERIC="yes" IPTABLES_STATUS_VERBOSE="no" IPTABLES_STATUS_LINENUMBERS="yes" IPTABLES_SYSCTL_LOAD_LIST="" # Load firewall configuration. [ -f "$IPTABLES_CONFIG" ] && . "$IPTABLES_CONFIG" # Netfilter modules NF_MODULES=($(lsmod | awk "/^${IPV}table_/ {print \$1}") ${IPV}_tables) NF_MODULES_COMMON=(x_tables nf_nat nf_conntrack) # Used by netfilter v4 and v6 # Get active tables NF_TABLES=$(cat "$PROC_IPTABLES_NAMES" 2>/dev/null) rmmod_r() { # Unload module with all referring modules. # At first all referring modules will be unloaded, then the module itself. local mod=$1 local ret=0 local ref= # Get referring modules. # New modutils have another output format. [ $NEW_MODUTILS = 1 ] \ && ref=$(lsmod | awk "/^${mod}/ { print \$4; }" | tr ',' ' ') \ || ref=$(lsmod | grep ^${mod} | cut -d "[" -s -f 2 | cut -d "]" -s -f 1) # recursive call for all referring modules for i in $ref; do rmmod_r $i let ret+=$?; done # Unload module. # The extra test is for 2.6: The module might have autocleaned, # after all referring modules are unloaded. if grep -q "^${mod}" /proc/modules ; then modprobe -r $mod > /dev/null 2>&1 res=$? [ $res -eq 0 ] || echo -n " $mod" let ret+=$res; fi return $ret } flush_n_delete() { # Flush firewall rules and delete chains. [ ! -e "$PROC_IPTABLES_NAMES" ] && return 0 # Check if firewall is configured (has tables) [ -z "$NF_TABLES" ] && return 1 echo -n $"${IPTABLES}: Flushing firewall rules: " ret=0 # For all tables for i in $NF_TABLES; do # Flush firewall rules. $IPTABLES -t $i -F; let ret+=$?; # Delete firewall chains. $IPTABLES -t $i -X; let ret+=$?; # Set counter to zero. $IPTABLES -t $i -Z; let ret+=$?; done [ $ret -eq 0 ] && success || failure echo return $ret } set_policy() { # Set policy for configured tables. policy=$1 # Check if iptable module is loaded [ ! -e "$PROC_IPTABLES_NAMES" ] && return 0 # Check if firewall is configured (has tables) tables=$(cat "$PROC_IPTABLES_NAMES" 2>/dev/null) [ -z "$tables" ] && return 1 echo -n $"${IPTABLES}: Setting chains to policy $policy: " ret=0 for i in $tables; do echo -n "$i " case "$i" in raw) $IPTABLES -t raw -P PREROUTING $policy \ && $IPTABLES -t raw -P OUTPUT $policy \ || let ret+=1 ;; filter) $IPTABLES -t filter -P INPUT $policy \ && $IPTABLES -t filter -P OUTPUT $policy \ && $IPTABLES -t filter -P FORWARD $policy \ || let ret+=1 ;; nat) $IPTABLES -t nat -P PREROUTING $policy \ && $IPTABLES -t nat -P POSTROUTING $policy \ && $IPTABLES -t nat -P OUTPUT $policy \ || let ret+=1 ;; mangle) $IPTABLES -t mangle -P PREROUTING $policy \ && $IPTABLES -t mangle -P POSTROUTING $policy \ && $IPTABLES -t mangle -P INPUT $policy \ && $IPTABLES -t mangle -P OUTPUT $policy \ && $IPTABLES -t mangle -P FORWARD $policy \ || let ret+=1 ;; *) let ret+=1 ;; esac done [ $ret -eq 0 ] && success || failure echo return $ret } load_sysctl() { # load matched sysctl values if [ -n "$IPTABLES_SYSCTL_LOAD_LIST" ]; then echo -n $"Loading sysctl settings: " ret=0 for item in $IPTABLES_SYSCTL_LOAD_LIST; do fgrep $item /etc/sysctl.conf | sysctl -p - >/dev/null let ret+=$?; done [ $ret -eq 0 ] && success || failure echo fi return $ret } start() { # Do not start if there is no config file. if [ ! -f "$IPTABLES_DATA" ]; then echo -n $"${IPTABLES}: No config file."; warning; echo return 6 fi # check if ipv6 module load is deactivated if [ "${_IPV}" = "ipv6" ] \ && grep -qIsE "^install[[:space:]]+${_IPV}[[:space:]]+/bin/(true|false)" /etc/modprobe.conf /etc/modprobe.d/* ; then echo $"${IPTABLES}: ${_IPV} is disabled." return 150 fi echo -n $"${IPTABLES}: Applying firewall rules: " OPT= [ "x$IPTABLES_SAVE_COUNTER" = "xyes" ] && OPT="-c" $IPTABLES-restore $OPT $IPTABLES_DATA if [ $? -eq 0 ]; then success; echo else failure; echo; if [ -f "$IPTABLES_FALLBACK_DATA" ]; then echo -n $"${IPTABLES}: Applying firewall fallback rules: " $IPTABLES-restore $OPT $IPTABLES_FALLBACK_DATA if [ $? -eq 0 ]; then success; echo else failure; echo; return 1 fi else return 1 fi fi # Load additional modules (helpers) if [ -n "$IPTABLES_MODULES" ]; then echo -n $"${IPTABLES}: Loading additional modules: " ret=0 for mod in $IPTABLES_MODULES; do echo -n "$mod " modprobe $mod > /dev/null 2>&1 let ret+=$?; done [ $ret -eq 0 ] && success || failure echo fi # Load sysctl settings load_sysctl touch $VAR_SUBSYS_IPTABLES return $ret } stop() { # Do not stop if iptables module is not loaded. [ ! -e "$PROC_IPTABLES_NAMES" ] && return 0 # Set default chain policy to ACCEPT, in order to not break shutdown # on systems where the default policy is DROP and root device is # network-based (i.e.: iSCSI, NFS) set_policy ACCEPT # And then, flush the rules and delete chains flush_n_delete if [ "x$IPTABLES_MODULES_UNLOAD" = "xyes" ]; then echo -n $"${IPTABLES}: Unloading modules: " ret=0 for mod in ${NF_MODULES[*]}; do rmmod_r $mod let ret+=$?; done # try to unload remaining netfilter modules used by ipv4 and ipv6 # netfilter for mod in ${NF_MODULES_COMMON[*]}; do rmmod_r $mod >/dev/null done [ $ret -eq 0 ] && success || failure echo fi rm -f $VAR_SUBSYS_IPTABLES return $ret } save() { # Check if iptable module is loaded if [ ! -e "$PROC_IPTABLES_NAMES" ]; then echo -n $"${IPTABLES}: Nothing to save."; warning; echo return 0 fi # Check if firewall is configured (has tables) if [ -z "$NF_TABLES" ]; then echo -n $"${IPTABLES}: Nothing to save."; warning; echo return 6 fi echo -n $"${IPTABLES}: Saving firewall rules to $IPTABLES_DATA: " OPT= [ "x$IPTABLES_SAVE_COUNTER" = "xyes" ] && OPT="-c" ret=0 TMP_FILE=$(/bin/mktemp -q $IPTABLES_DATA.XXXXXX) \ && chmod 600 "$TMP_FILE" \ && $IPTABLES-save $OPT > $TMP_FILE 2>/dev/null \ && size=$(stat -c '%s' $TMP_FILE) && [ $size -gt 0 ] \ || ret=1 if [ $ret -eq 0 ]; then if [ -e $IPTABLES_DATA ]; then cp -f $IPTABLES_DATA $IPTABLES_DATA.save \ && chmod 600 $IPTABLES_DATA.save \ && restorecon $IPTABLES_DATA.save \ || ret=1 fi if [ $ret -eq 0 ]; then mv -f $TMP_FILE $IPTABLES_DATA \ && chmod 600 $IPTABLES_DATA \ && restorecon $IPTABLES_DATA \ || ret=1 fi fi rm -f $TMP_FILE [ $ret -eq 0 ] && success || failure echo return $ret } status() { if [ ! -f "$VAR_SUBSYS_IPTABLES" -a -z "$NF_TABLES" ]; then echo $"${IPTABLES}: Firewall is not running." return 3 fi # Do not print status if lockfile is missing and iptables modules are not # loaded. # Check if iptable modules are loaded if [ ! -e "$PROC_IPTABLES_NAMES" ]; then echo $"${IPTABLES}: Firewall modules are not loaded." return 3 fi # Check if firewall is configured (has tables) if [ -z "$NF_TABLES" ]; then echo $"${IPTABLES}: Firewall is not configured. " return 3 fi NUM= [ "x$IPTABLES_STATUS_NUMERIC" = "xyes" ] && NUM="-n" VERBOSE= [ "x$IPTABLES_STATUS_VERBOSE" = "xyes" ] && VERBOSE="--verbose" COUNT= [ "x$IPTABLES_STATUS_LINENUMBERS" = "xyes" ] && COUNT="--line-numbers" for table in $NF_TABLES; do echo $"Table: $table" $IPTABLES -t $table --list $NUM $VERBOSE $COUNT && echo done return 0 } reload() { # Do not reload if there is no config file. if [ ! -f "$IPTABLES_DATA" ]; then echo -n $"${IPTABLES}: No config file."; warning; echo return 6 fi # check if ipv6 module load is deactivated if [ "${_IPV}" = "ipv6" ] \ && grep -qIsE "^install[[:space:]]+${_IPV}[[:space:]]+/bin/(true|false)" /etc/modprobe.conf /etc/modprobe.d/* ; then echo $"${IPTABLES}: ${_IPV} is disabled." return 150 fi echo -n $"${IPTABLES}: Trying to reload firewall rules: " OPT= [ "x$IPTABLES_SAVE_COUNTER" = "xyes" ] && OPT="-c" $IPTABLES-restore $OPT $IPTABLES_DATA if [ $? -eq 0 ]; then success; echo else failure; echo; echo "Firewall rules are not changed."; return 1 fi # Load additional modules (helpers) if [ -n "$IPTABLES_MODULES" ]; then echo -n $"${IPTABLES}: Loading additional modules: " ret=0 for mod in $IPTABLES_MODULES; do echo -n "$mod " modprobe $mod > /dev/null 2>&1 let ret+=$?; done [ $ret -eq 0 ] && success || failure echo fi # Load sysctl settings load_sysctl return $ret } restart() { [ "x$IPTABLES_SAVE_ON_RESTART" = "xyes" ] && save stop start } case "$1" in start) [ -f "$VAR_SUBSYS_IPTABLES" ] && exit 0 start RETVAL=$? ;; stop) [ "x$IPTABLES_SAVE_ON_STOP" = "xyes" ] && save stop RETVAL=$? ;; restart|force-reload) restart RETVAL=$? ;; reload) [ -e "$VAR_SUBSYS_IPTABLES" ] && reload RETVAL=$? ;; condrestart|try-restart) [ ! -e "$VAR_SUBSYS_IPTABLES" ] && exit 0 restart RETVAL=$? ;; status) status RETVAL=$? ;; panic) set_policy DROP RETVAL=$? ;; save) save RETVAL=$? ;; *) echo $"Usage: ${IPTABLES} {start|stop|reload|restart|condrestart|status|panic|save}" RETVAL=2 ;; esac exit $RETVAL -
 SSH端口修改 高危机房的SSH端口常被封,即便是正常的SSH以及Sftp流量,因此需要更换SSH端口以便管理服务器。已确认高危IDC机房:Choopa,阿里云香港等。修改方法一:默认情况下用vi编辑/etc/ssh/sshd_config将#Port 22这行的井字号去除,把22更改为新端口后保存即可。最后运行命令重启ssh进程/etc/init.d/sshd restsrtcentos7则是systemctl restart sshd方法二:对于不熟悉vi等编辑器的,可使用sed命令快速修改sed -i 's/Port 你当前的端口/Port 新端口/g' /etc/ssh/sshd_config执行命令完毕后如方法一重启ssh进程即可
SSH端口修改 高危机房的SSH端口常被封,即便是正常的SSH以及Sftp流量,因此需要更换SSH端口以便管理服务器。已确认高危IDC机房:Choopa,阿里云香港等。修改方法一:默认情况下用vi编辑/etc/ssh/sshd_config将#Port 22这行的井字号去除,把22更改为新端口后保存即可。最后运行命令重启ssh进程/etc/init.d/sshd restsrtcentos7则是systemctl restart sshd方法二:对于不熟悉vi等编辑器的,可使用sed命令快速修改sed -i 's/Port 你当前的端口/Port 新端口/g' /etc/ssh/sshd_config执行命令完毕后如方法一重启ssh进程即可 -
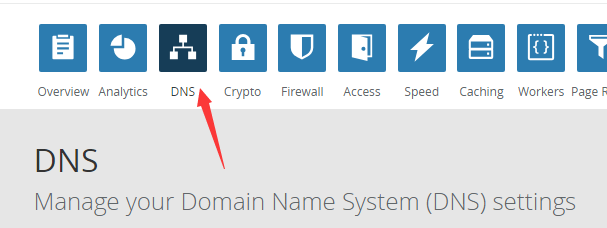
 基于CloudFlare API的纯Shell动态DNS(DDNS)脚本 家庭宽带的IP是不固定的,当出门在外,人不在家时,一旦IP变动,就给接入家中的设备(如监控)带来许多麻烦,于是我编写了一个能在Linux系统下运行,基于cloudflare API的动态DNS脚本,虽然国内已有花生壳之类的ddns服务,但是那些实在是太坑爹,比如只能使用它提供的二级域名,而该脚本能够配置顶级域名的动态DNS解析。使用前提:局域网内有Linux主机(如openwrt路由设备)、有一个顶级域名、域名解析必须由CloudFlare托管。使用方法:步骤一:到CloudFlare官网注册一个帐号,找到DNS选项,如下图箭头指向,根据其要求,到你的域名注册商处将DNS服务器修改为CloudFlare提供的地址,修改完验证成功后就可以开始解析了。步骤三:获取三个Key值,其中APIKey和ZoneID可在官网登录后的Overview页面获得,而DNSID获取较为复杂,具体命令如下(需要安装curl):curl -X GET "https://api.cloudflare.com/client/v4/zones/输入你的ZoneID/dns_records?type=A&name=刚才设置的记录值(比如xxx.yourdomain.com)" \ -H "X-Auth-Email:你注册时的邮箱" \ -H "X-Auth-Key:你的APIKEY" \ -H "Content-Type: application/json"运行该命令后会输出结果,找到"id":"xxx"这个选项,其中的xxx即对应你的DNSID值下方为shell脚本(需要设备安装curl),配置好后可利用crontab命令定时执行,(1-2分钟执行一次最佳)具体操作如下:crontab -e */2 * * * * 脚本存放目录cfddns.sh#!/bin/sh CF_API_KEY=输入你的APIKEY CF_ZONE_ID=输入你的ZONEID CF_DNS_ID=输入你的解析记录值对应的DNSID EMAIL=输入你注册时的邮箱 ROUTER_NETWORK_DEVICE=你的设备拨号的网卡,openwrt一般是pppoe,可使用ifconfig命令查看 TEMP_FILE_PATH=/tmp/cloudflare-ddns/DNS_RECORD=填写用于ddns的DNS记录,要完整填写,比如:xxx.yourdomain.com mkdir -p ${TEMP_FILE_PATH}curl -k -X GET "https://api.cloudflare.com/client/v4/zones/${CF_ZONE_ID}/dns_records/${CF_DNS_ID}" \ -H "X-Auth-Email:${EMAIL}" \ -H "X-Auth-Key:${CF_API_KEY}" \ -H "Content-Type: application/json" |awk -F '"' '{print $26}'>${TEMP_FILE_PATH}/current_resolving.txt ifconfig $ROUTER_NETWORK_DEVICE | awk -F'[ ]+|:' '/inet /{print $4}'>${TEMP_FILE_PATH}/current_ip.txt if [ "$(cat ${TEMP_FILE_PATH}/current_ip.txt)" == "$(cat ${TEMP_FILE_PATH}/current_resolving.txt)" ]; then exit 1 else CURRENT_IP="$(cat ${TEMP_FILE_PATH}/current_ip.txt)" curl -k -X PUT "https://api.cloudflare.com/client/v4/zones/${CF_ZONE_ID}/dns_records/${CF_DNS_ID}" \ -H "X-Auth-Email:${EMAIL}" \ -H "X-Auth-Key:${CF_API_KEY}" \ -H "Content-Type: application/json" \ --data '{"type":"A","name":"'$DNS_RECORD'","content":"'$CURRENT_IP'","ttl":1,"proxied":false}' fi
基于CloudFlare API的纯Shell动态DNS(DDNS)脚本 家庭宽带的IP是不固定的,当出门在外,人不在家时,一旦IP变动,就给接入家中的设备(如监控)带来许多麻烦,于是我编写了一个能在Linux系统下运行,基于cloudflare API的动态DNS脚本,虽然国内已有花生壳之类的ddns服务,但是那些实在是太坑爹,比如只能使用它提供的二级域名,而该脚本能够配置顶级域名的动态DNS解析。使用前提:局域网内有Linux主机(如openwrt路由设备)、有一个顶级域名、域名解析必须由CloudFlare托管。使用方法:步骤一:到CloudFlare官网注册一个帐号,找到DNS选项,如下图箭头指向,根据其要求,到你的域名注册商处将DNS服务器修改为CloudFlare提供的地址,修改完验证成功后就可以开始解析了。步骤三:获取三个Key值,其中APIKey和ZoneID可在官网登录后的Overview页面获得,而DNSID获取较为复杂,具体命令如下(需要安装curl):curl -X GET "https://api.cloudflare.com/client/v4/zones/输入你的ZoneID/dns_records?type=A&name=刚才设置的记录值(比如xxx.yourdomain.com)" \ -H "X-Auth-Email:你注册时的邮箱" \ -H "X-Auth-Key:你的APIKEY" \ -H "Content-Type: application/json"运行该命令后会输出结果,找到"id":"xxx"这个选项,其中的xxx即对应你的DNSID值下方为shell脚本(需要设备安装curl),配置好后可利用crontab命令定时执行,(1-2分钟执行一次最佳)具体操作如下:crontab -e */2 * * * * 脚本存放目录cfddns.sh#!/bin/sh CF_API_KEY=输入你的APIKEY CF_ZONE_ID=输入你的ZONEID CF_DNS_ID=输入你的解析记录值对应的DNSID EMAIL=输入你注册时的邮箱 ROUTER_NETWORK_DEVICE=你的设备拨号的网卡,openwrt一般是pppoe,可使用ifconfig命令查看 TEMP_FILE_PATH=/tmp/cloudflare-ddns/DNS_RECORD=填写用于ddns的DNS记录,要完整填写,比如:xxx.yourdomain.com mkdir -p ${TEMP_FILE_PATH}curl -k -X GET "https://api.cloudflare.com/client/v4/zones/${CF_ZONE_ID}/dns_records/${CF_DNS_ID}" \ -H "X-Auth-Email:${EMAIL}" \ -H "X-Auth-Key:${CF_API_KEY}" \ -H "Content-Type: application/json" |awk -F '"' '{print $26}'>${TEMP_FILE_PATH}/current_resolving.txt ifconfig $ROUTER_NETWORK_DEVICE | awk -F'[ ]+|:' '/inet /{print $4}'>${TEMP_FILE_PATH}/current_ip.txt if [ "$(cat ${TEMP_FILE_PATH}/current_ip.txt)" == "$(cat ${TEMP_FILE_PATH}/current_resolving.txt)" ]; then exit 1 else CURRENT_IP="$(cat ${TEMP_FILE_PATH}/current_ip.txt)" curl -k -X PUT "https://api.cloudflare.com/client/v4/zones/${CF_ZONE_ID}/dns_records/${CF_DNS_ID}" \ -H "X-Auth-Email:${EMAIL}" \ -H "X-Auth-Key:${CF_API_KEY}" \ -H "Content-Type: application/json" \ --data '{"type":"A","name":"'$DNS_RECORD'","content":"'$CURRENT_IP'","ttl":1,"proxied":false}' fi -
 一次LNMP安装笔记 新开了一台虚拟机测试机,于是进行了LNMP安装测试,以下是编译笔记。系统环境:CentOS6-X86_64MySQL版本:5.6.39Nginx版本:1.12.2PHP版本5.6.35安装LNMP所需依赖yum install -y gcc gcc-c++ bison-devel ncurses-devel perl cmake pcre pcre-devel openssl openssl-devel zlib zlib-devel automake libcurl curl-devel bzip2 bzip2-devel libjpeg libjpeg-devel libpng libpng-devel freetype freetype-devel libxml2 libxml2-devel mcrypt mhash mhash-devel readline-devel libedit-devel sqlite-devel libiconv libmcrypt libmcrypt-devel icu libicu libicu-devel libxslt libxslt-devel编译MySQLcd /usr/src wget https://mirrors.ustc.edu.cn/mysql-ftp/Downloads/MySQL-5.6/mysql-5.6.39.tar.gz tar -zxvf mysql-5.6.39.tar.gz group add mysql useradd -s /sbin/nologin -g mysql mysql mkdir -p /usr/local/mysql/ cd /usr/src/mysql-5.6.39 cmake -DCMAKE_INSTALL_PREFIX=/usr/local/mysql -DMYSQL_DATADIR=/usr/local/mysql/data -DSYSCONFDIR=/etc -DWITH_MYISAM_STORAGE_ENGINE=1 -DWITH_INNOBASE_STORAGE_ENGINE=1 -DWITH_MEMORY_STORAGE_ENGINE=1 -DWITH_READLINE=1 -DMYSQL_TCP_PORT=3306 -DENABLED_LOCAL_INFILE=1 -DWITH_PARTITION_STORAGE_ENGINE=1 -DEXTRA_CHARSETS=all -DWITH_FEDERATED_STORAGE_ENGINE=1 -DEXTRA_CHARSETS=all -DDEFAULT_CHARSET=utf8mb4 -DDEFAULT_COLLATION=utf8mb4_general_ci -DWITH_EMBEDDED_SERVER=1 make && make install /usr/local/mysql/scripts ln -s /usr/local/mysql/bin/mysql /usr/bin/mysql ln -s /usr/local/mysql/bin/mysqlcheck /usr/bin/mysqlcheck ln -s /usr/local/mysql/bin/mysqld_safe /usr/bin/mysqld_safe ln -s /usr/local/mysql/bin/mysqldump /usr/bin/mysqldump ln -s /usr/local/mysql/support-files/mysql.server /etc/init.d/mysql编译Nginxcd /usr/src wget http://nginx.org/download/nginx-1.12.2.tar.gz tar -zxvf nginx-1.12.2.tar.gz groupadd www useradd -s /sbin/nologin -g www www mkdir -p /usr/local/nginx cd /usr/src/nginx-1.12.2 ./configure --prefix=/usr/local/nginx --sbin-path=/usr/local/nginx/sbin/nginx --conf-path=/usr/local/nginx/conf/nginx.conf --error-log-path=/usr/local/nginx/log/error.log --http-log-path=/home/wwwlogs/access.log --pid-path=/var/run/nginx.pid --lock-path=/var/lock/nginx.lock --user=www --group=www --with-http_ssl_module --with-http_sub_module --with-http_stub_status_module --with-http_gzip_static_module --http-client-body-temp-path=/usr/local/nginx/temp/client/ --http-proxy-temp-path=/usr/local/nginx/temp/proxy/ --http-fastcgi-temp-path=/usr/local/nginx/temp/fcgi/ --http-uwsgi-temp-path=/usr/local/nginx/temp/uwsgi --http-scgi-temp-path=/usr/local/nginx/temp/scgi --with-pcre make && make install编译PHPmkdir -p /usr/local/php cd /usr/src wget http://cn2.php.net/distributions/php-5.6.35.tar.gz tar -zxvf php-5.6.35.tar.gz cd php-5.6.35/ ./configure --prefix=/usr/local/php --with-config-file-path=/usr/local/php/etc --with-config-file-scan-dir=/usr/local/php/conf.d --enable-fpm --with-fpm-user=www --with-fpm-group=www --with-mysql=mysqlnd --with-mysqli=mysqlnd --with-pdo-mysql=mysqlnd --with-iconv-dir --with-freetype-dir=/usr/local/freetype --with-jpeg-dir --with-png-dir --with-zlib --with-libxml-dir=/usr --enable-xml --disable-rpath --enable-bcmath --enable-shmop --enable-sysvsem --enable-inline-optimization --with-curl --enable-mbregex --enable-mbstring --with-mcrypt --enable-ftp --with-gd --enable-gd-native-ttf --with-openssl --with-mhash --enable-pcntl --enable-sockets --with-xmlrpc --enable-zip --enable-soap --with-gettext --disable-fileinfo --enable-opcache --enable-intl --with-xsl make && make install cp /usr/src/php-5.6.35/php.ini-production /usr/local/php/etc/php.ini cp /usr/src/php-5.6.35/sapi/fpm/init.d.php-fpm /etc/init.d/php-fpm如果编译出现libiconv错误则在/usr/src/php-5.6.35/Makefile文件此行末尾添加-liconvEXTRA_LIBS = -lcrypt -lz -lexslt -lresolv -lcrypt -lrt -lmcrypt -lstdc++ -lpng -lz -ljpeg -lcurl -lz -lrt -lm -ldl -lnsl -lxml2 -lz -lm -ldl -lssl -lcrypto -lcurl -lxml2 -lz -lm -ldl -lssl -lcrypto -lfreetype -ldl -lm -licui18n -licuuc -licudata -ldl -lm -licuio -lxml2 -lz -lm -ldl -lxml2 -lz -lm -ldl -lcrypt -lxml2 -lz -lm -ldl -lxml2 -lz -lm -ldl -lxml2 -lz -lm -ldl -lxml2 -lz -lm -ldl -lxslt -lxml2 -lz -ldl -lm -lssl -lcrypto -lcrypt -liconv编辑Nginx的配置由于配置较为复杂,因此参考了军哥LNMP一键安装包的配置user www www; worker_processes 1; worker_rlimit_nofile 65535; error_log logs/error.log; error_log logs/error.log notice; error_log logs/error.log info; pid logs/nginx.pid; events { worker_connections 65535; use epoll; } http { include mime.types; default_type application/octet-stream; server_names_hash_bucket_size 128; client_header_buffer_size 32k; large_client_header_buffers 4 32k; client_max_body_size 300m; tcp_nopush on; keepalive_timeout 60; tcp_nodelay on; server_tokens off; gzip on; gzip_min_length 1k; gzip_buffers 4 16k; gzip_http_version 1.1; gzip_comp_level 2; gzip_types text/plain application/x-javascript text/css application/xml; gzip_vary on; log_format main '$remote_addr - $remote_user [$time_local] "$request" ' '$status $body_bytes_sent "$http_referer" ' '"$http_user_agent" "$http_x_forwarded_for"'; gzip on; include vhost/*.conf; } #在一个server字段中打开PHP支持 location ~ [^/]\.php(/|$) { try_files $uri =404; fastcgi_pass unix:/tmp/php-cgi.sock; fastcgi_index index.php; include fastcgi.conf; }附nginx启动脚本,脚本来自LNMP一键安装包#! /bin/sh # chkconfig: 2345 55 25 # Description: Startup script for nginx webserver on Debian. Place in /etc/init.d and # run 'update-rc.d -f nginx defaults', or use the appropriate command on your # distro. For CentOS/Redhat run: 'chkconfig --add nginx' ### BEGIN INIT INFO # Provides: nginx # Required-Start: $all # Required-Stop: $all # Default-Start: 2 3 4 5 # Default-Stop: 0 1 6 # Short-Description: starts the nginx web server # Description: starts nginx using start-stop-daemon ### END INIT INFO # Author: licess # website: https://lnmp.org PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin NAME=nginx NGINX_BIN=/usr/local/nginx/sbin/$NAME CONFIGFILE=/usr/local/nginx/conf/$NAME.conf PIDFILE=/usr/local/nginx/logs/$NAME.pid if [ -s /bin/ss ]; then StatBin=/bin/ss else StatBin=/bin/netstat fi case "$1" in start) echo -n "Starting $NAME... " if $StatBin -tnpl | grep -q nginx;then echo "$NAME (pid `pidof $NAME`) already running." exit 1 fi $NGINX_BIN -c $CONFIGFILE if [ "$?" != 0 ] ; then echo " failed" exit 1 else echo " done" fi ;; stop) echo -n "Stoping $NAME... " if ! $StatBin -tnpl | grep -q nginx; then echo "$NAME is not running." exit 1 fi $NGINX_BIN -s stop if [ "$?" != 0 ] ; then echo " failed. Use force-quit" exit 1 else echo " done" fi ;; status) if $StatBin -tnpl | grep -q nginx; then PID=`pidof nginx` echo "$NAME (pid $PID) is running..." else echo "$NAME is stopped." exit 0 fi ;; force-quit|kill) echo -n "Terminating $NAME... " if ! $StatBin -tnpl | grep -q nginx; then echo "$NAME is is stopped." exit 1 fi kill `pidof $NAME` if [ "$?" != 0 ] ; then echo " failed" exit 1 else echo " done" fi ;; restart) $0 stop sleep 1 $0 start ;; reload) echo -n "Reload service $NAME... " if $StatBin -tnpl | grep -q nginx; then $NGINX_BIN -s reload echo " done" else echo "$NAME is not running, can't reload." exit 1 fi ;; configtest) echo -n "Test $NAME configure files... " $NGINX_BIN -t ;; *) echo "Usage: $0 {start|stop|restart|reload|status|configtest|force-quit|kill}" exit 1 ;; esac
一次LNMP安装笔记 新开了一台虚拟机测试机,于是进行了LNMP安装测试,以下是编译笔记。系统环境:CentOS6-X86_64MySQL版本:5.6.39Nginx版本:1.12.2PHP版本5.6.35安装LNMP所需依赖yum install -y gcc gcc-c++ bison-devel ncurses-devel perl cmake pcre pcre-devel openssl openssl-devel zlib zlib-devel automake libcurl curl-devel bzip2 bzip2-devel libjpeg libjpeg-devel libpng libpng-devel freetype freetype-devel libxml2 libxml2-devel mcrypt mhash mhash-devel readline-devel libedit-devel sqlite-devel libiconv libmcrypt libmcrypt-devel icu libicu libicu-devel libxslt libxslt-devel编译MySQLcd /usr/src wget https://mirrors.ustc.edu.cn/mysql-ftp/Downloads/MySQL-5.6/mysql-5.6.39.tar.gz tar -zxvf mysql-5.6.39.tar.gz group add mysql useradd -s /sbin/nologin -g mysql mysql mkdir -p /usr/local/mysql/ cd /usr/src/mysql-5.6.39 cmake -DCMAKE_INSTALL_PREFIX=/usr/local/mysql -DMYSQL_DATADIR=/usr/local/mysql/data -DSYSCONFDIR=/etc -DWITH_MYISAM_STORAGE_ENGINE=1 -DWITH_INNOBASE_STORAGE_ENGINE=1 -DWITH_MEMORY_STORAGE_ENGINE=1 -DWITH_READLINE=1 -DMYSQL_TCP_PORT=3306 -DENABLED_LOCAL_INFILE=1 -DWITH_PARTITION_STORAGE_ENGINE=1 -DEXTRA_CHARSETS=all -DWITH_FEDERATED_STORAGE_ENGINE=1 -DEXTRA_CHARSETS=all -DDEFAULT_CHARSET=utf8mb4 -DDEFAULT_COLLATION=utf8mb4_general_ci -DWITH_EMBEDDED_SERVER=1 make && make install /usr/local/mysql/scripts ln -s /usr/local/mysql/bin/mysql /usr/bin/mysql ln -s /usr/local/mysql/bin/mysqlcheck /usr/bin/mysqlcheck ln -s /usr/local/mysql/bin/mysqld_safe /usr/bin/mysqld_safe ln -s /usr/local/mysql/bin/mysqldump /usr/bin/mysqldump ln -s /usr/local/mysql/support-files/mysql.server /etc/init.d/mysql编译Nginxcd /usr/src wget http://nginx.org/download/nginx-1.12.2.tar.gz tar -zxvf nginx-1.12.2.tar.gz groupadd www useradd -s /sbin/nologin -g www www mkdir -p /usr/local/nginx cd /usr/src/nginx-1.12.2 ./configure --prefix=/usr/local/nginx --sbin-path=/usr/local/nginx/sbin/nginx --conf-path=/usr/local/nginx/conf/nginx.conf --error-log-path=/usr/local/nginx/log/error.log --http-log-path=/home/wwwlogs/access.log --pid-path=/var/run/nginx.pid --lock-path=/var/lock/nginx.lock --user=www --group=www --with-http_ssl_module --with-http_sub_module --with-http_stub_status_module --with-http_gzip_static_module --http-client-body-temp-path=/usr/local/nginx/temp/client/ --http-proxy-temp-path=/usr/local/nginx/temp/proxy/ --http-fastcgi-temp-path=/usr/local/nginx/temp/fcgi/ --http-uwsgi-temp-path=/usr/local/nginx/temp/uwsgi --http-scgi-temp-path=/usr/local/nginx/temp/scgi --with-pcre make && make install编译PHPmkdir -p /usr/local/php cd /usr/src wget http://cn2.php.net/distributions/php-5.6.35.tar.gz tar -zxvf php-5.6.35.tar.gz cd php-5.6.35/ ./configure --prefix=/usr/local/php --with-config-file-path=/usr/local/php/etc --with-config-file-scan-dir=/usr/local/php/conf.d --enable-fpm --with-fpm-user=www --with-fpm-group=www --with-mysql=mysqlnd --with-mysqli=mysqlnd --with-pdo-mysql=mysqlnd --with-iconv-dir --with-freetype-dir=/usr/local/freetype --with-jpeg-dir --with-png-dir --with-zlib --with-libxml-dir=/usr --enable-xml --disable-rpath --enable-bcmath --enable-shmop --enable-sysvsem --enable-inline-optimization --with-curl --enable-mbregex --enable-mbstring --with-mcrypt --enable-ftp --with-gd --enable-gd-native-ttf --with-openssl --with-mhash --enable-pcntl --enable-sockets --with-xmlrpc --enable-zip --enable-soap --with-gettext --disable-fileinfo --enable-opcache --enable-intl --with-xsl make && make install cp /usr/src/php-5.6.35/php.ini-production /usr/local/php/etc/php.ini cp /usr/src/php-5.6.35/sapi/fpm/init.d.php-fpm /etc/init.d/php-fpm如果编译出现libiconv错误则在/usr/src/php-5.6.35/Makefile文件此行末尾添加-liconvEXTRA_LIBS = -lcrypt -lz -lexslt -lresolv -lcrypt -lrt -lmcrypt -lstdc++ -lpng -lz -ljpeg -lcurl -lz -lrt -lm -ldl -lnsl -lxml2 -lz -lm -ldl -lssl -lcrypto -lcurl -lxml2 -lz -lm -ldl -lssl -lcrypto -lfreetype -ldl -lm -licui18n -licuuc -licudata -ldl -lm -licuio -lxml2 -lz -lm -ldl -lxml2 -lz -lm -ldl -lcrypt -lxml2 -lz -lm -ldl -lxml2 -lz -lm -ldl -lxml2 -lz -lm -ldl -lxml2 -lz -lm -ldl -lxslt -lxml2 -lz -ldl -lm -lssl -lcrypto -lcrypt -liconv编辑Nginx的配置由于配置较为复杂,因此参考了军哥LNMP一键安装包的配置user www www; worker_processes 1; worker_rlimit_nofile 65535; error_log logs/error.log; error_log logs/error.log notice; error_log logs/error.log info; pid logs/nginx.pid; events { worker_connections 65535; use epoll; } http { include mime.types; default_type application/octet-stream; server_names_hash_bucket_size 128; client_header_buffer_size 32k; large_client_header_buffers 4 32k; client_max_body_size 300m; tcp_nopush on; keepalive_timeout 60; tcp_nodelay on; server_tokens off; gzip on; gzip_min_length 1k; gzip_buffers 4 16k; gzip_http_version 1.1; gzip_comp_level 2; gzip_types text/plain application/x-javascript text/css application/xml; gzip_vary on; log_format main '$remote_addr - $remote_user [$time_local] "$request" ' '$status $body_bytes_sent "$http_referer" ' '"$http_user_agent" "$http_x_forwarded_for"'; gzip on; include vhost/*.conf; } #在一个server字段中打开PHP支持 location ~ [^/]\.php(/|$) { try_files $uri =404; fastcgi_pass unix:/tmp/php-cgi.sock; fastcgi_index index.php; include fastcgi.conf; }附nginx启动脚本,脚本来自LNMP一键安装包#! /bin/sh # chkconfig: 2345 55 25 # Description: Startup script for nginx webserver on Debian. Place in /etc/init.d and # run 'update-rc.d -f nginx defaults', or use the appropriate command on your # distro. For CentOS/Redhat run: 'chkconfig --add nginx' ### BEGIN INIT INFO # Provides: nginx # Required-Start: $all # Required-Stop: $all # Default-Start: 2 3 4 5 # Default-Stop: 0 1 6 # Short-Description: starts the nginx web server # Description: starts nginx using start-stop-daemon ### END INIT INFO # Author: licess # website: https://lnmp.org PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin NAME=nginx NGINX_BIN=/usr/local/nginx/sbin/$NAME CONFIGFILE=/usr/local/nginx/conf/$NAME.conf PIDFILE=/usr/local/nginx/logs/$NAME.pid if [ -s /bin/ss ]; then StatBin=/bin/ss else StatBin=/bin/netstat fi case "$1" in start) echo -n "Starting $NAME... " if $StatBin -tnpl | grep -q nginx;then echo "$NAME (pid `pidof $NAME`) already running." exit 1 fi $NGINX_BIN -c $CONFIGFILE if [ "$?" != 0 ] ; then echo " failed" exit 1 else echo " done" fi ;; stop) echo -n "Stoping $NAME... " if ! $StatBin -tnpl | grep -q nginx; then echo "$NAME is not running." exit 1 fi $NGINX_BIN -s stop if [ "$?" != 0 ] ; then echo " failed. Use force-quit" exit 1 else echo " done" fi ;; status) if $StatBin -tnpl | grep -q nginx; then PID=`pidof nginx` echo "$NAME (pid $PID) is running..." else echo "$NAME is stopped." exit 0 fi ;; force-quit|kill) echo -n "Terminating $NAME... " if ! $StatBin -tnpl | grep -q nginx; then echo "$NAME is is stopped." exit 1 fi kill `pidof $NAME` if [ "$?" != 0 ] ; then echo " failed" exit 1 else echo " done" fi ;; restart) $0 stop sleep 1 $0 start ;; reload) echo -n "Reload service $NAME... " if $StatBin -tnpl | grep -q nginx; then $NGINX_BIN -s reload echo " done" else echo "$NAME is not running, can't reload." exit 1 fi ;; configtest) echo -n "Test $NAME configure files... " $NGINX_BIN -t ;; *) echo "Usage: $0 {start|stop|restart|reload|status|configtest|force-quit|kill}" exit 1 ;; esac -
 Let's Encrypt免费泛域名SSL证书获取 Let's Encrypt在2018年3月正式支持泛域名证书,使用泛域名的好处就是可以一键支持所有二级域名,不必再单独为二级域名创建SSL证书。之前是使用certbot通过随机生成一个文件到域名所对应的网站目录,然后letsencrypt的机器人会通过GET请求相应域名并获取该随机文件的方式来确保申请者对域名的控制权,个人觉得此办法及其麻烦,想要SSL证书服务器就必须开放http服务,而现在申请泛域名SSL证书的办法可通过使用acme.sh脚本来申请,该脚本的原理是通过DNS解析商提供的API来添加/删除一条域名的TXT记录,然后让CA机构进行验证,以确保申请者对域名的所有权。该方法不必使用http方式来申请,大大方便了SSL证书的申请过程。参考文档:https://github.com/Neilpang/acme.shhttps://github.com/Neilpang/acme.sh/blob/master/dnsapi/README.md(DNS API使用方法)wget -O - https://get.acme.sh | sh chmod +x acme.sh首次运行acme.sh脚本会初始化并生成一些通过NS提供商API修改记录的配置文件,在dnsapi目录下,如果你的NS解析商为阿里云,就先获取阿里云API Key,然后修改dnsapi目录内相对应的模板,填入对应的API Keyexport Ali_Key=xxxxx export Ali_Secret=xxxxx完成API Key的编辑后,就可以开始执行申请证书的命令./acme.sh --issue -d *.你的域名.com 你的域名.com --dns dns_ali如果申请成功,脚本会有提示在/root/.acme.sh/*.你的域名.com目录下可找到证书文件
Let's Encrypt免费泛域名SSL证书获取 Let's Encrypt在2018年3月正式支持泛域名证书,使用泛域名的好处就是可以一键支持所有二级域名,不必再单独为二级域名创建SSL证书。之前是使用certbot通过随机生成一个文件到域名所对应的网站目录,然后letsencrypt的机器人会通过GET请求相应域名并获取该随机文件的方式来确保申请者对域名的控制权,个人觉得此办法及其麻烦,想要SSL证书服务器就必须开放http服务,而现在申请泛域名SSL证书的办法可通过使用acme.sh脚本来申请,该脚本的原理是通过DNS解析商提供的API来添加/删除一条域名的TXT记录,然后让CA机构进行验证,以确保申请者对域名的所有权。该方法不必使用http方式来申请,大大方便了SSL证书的申请过程。参考文档:https://github.com/Neilpang/acme.shhttps://github.com/Neilpang/acme.sh/blob/master/dnsapi/README.md(DNS API使用方法)wget -O - https://get.acme.sh | sh chmod +x acme.sh首次运行acme.sh脚本会初始化并生成一些通过NS提供商API修改记录的配置文件,在dnsapi目录下,如果你的NS解析商为阿里云,就先获取阿里云API Key,然后修改dnsapi目录内相对应的模板,填入对应的API Keyexport Ali_Key=xxxxx export Ali_Secret=xxxxx完成API Key的编辑后,就可以开始执行申请证书的命令./acme.sh --issue -d *.你的域名.com 你的域名.com --dns dns_ali如果申请成功,脚本会有提示在/root/.acme.sh/*.你的域名.com目录下可找到证书文件